The upcoming Android 16 release introduces a critical new security feature: Network Notification Warnings This enhancement is designed to alert users in real time when their mobile devices are exposed […]

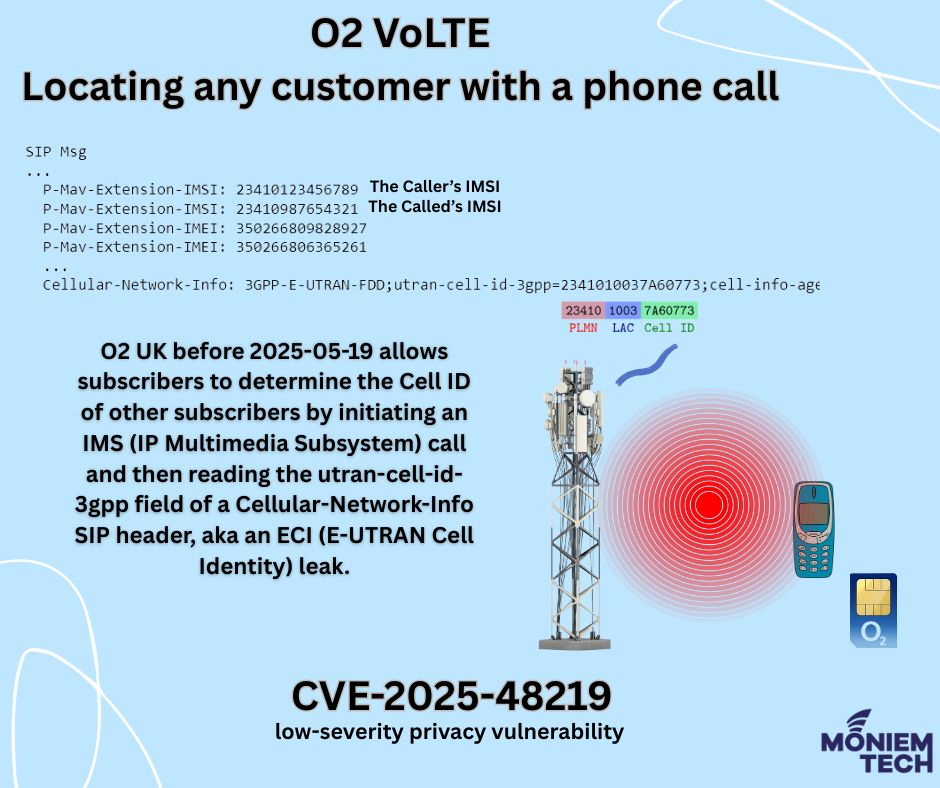
Vulnerability Details: CVE-2024-53026. It is a vulnerability affecting O2 UK’s VoLTE/IMS service, disclosed in mid-May 2025. Rated Low, with a CVSS v3 score of 3.5. It has a limited impact on confidentiality […]
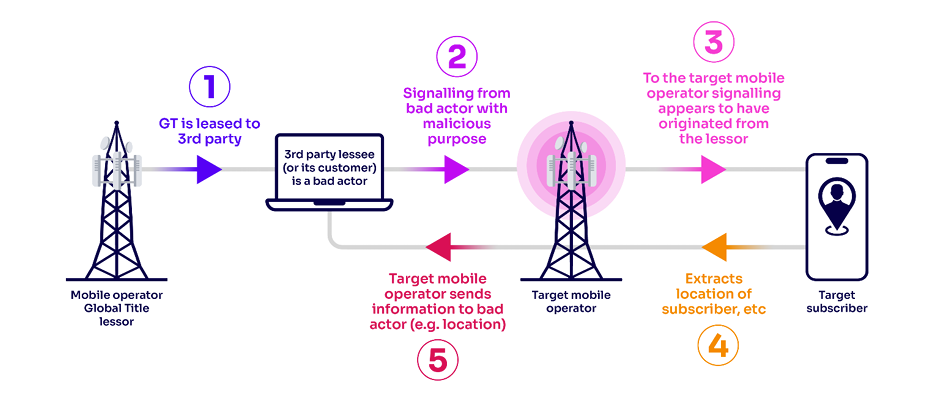
I wrote an article before about ” What is GT (Global Title)? Why Do We Need It?” What is Global Title Leasing? GT leasing is the practice of a mobile […]
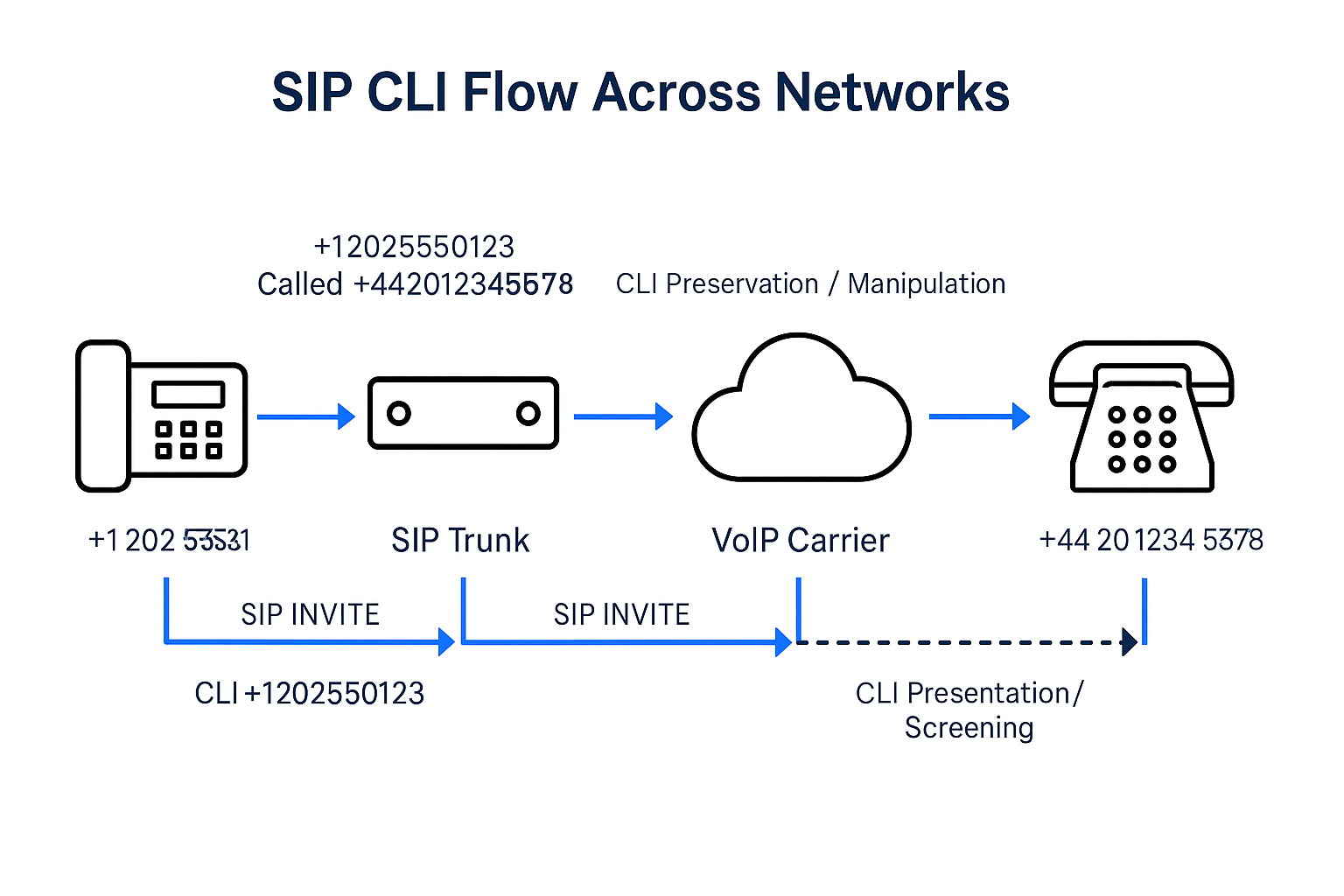
Last weekend, by coincidence, I found a fraud story related to the Telecom domain called “Spoofing CLI” or “Calling Line Identification (CLI) spoofing.” which is a technique used in mobile […]
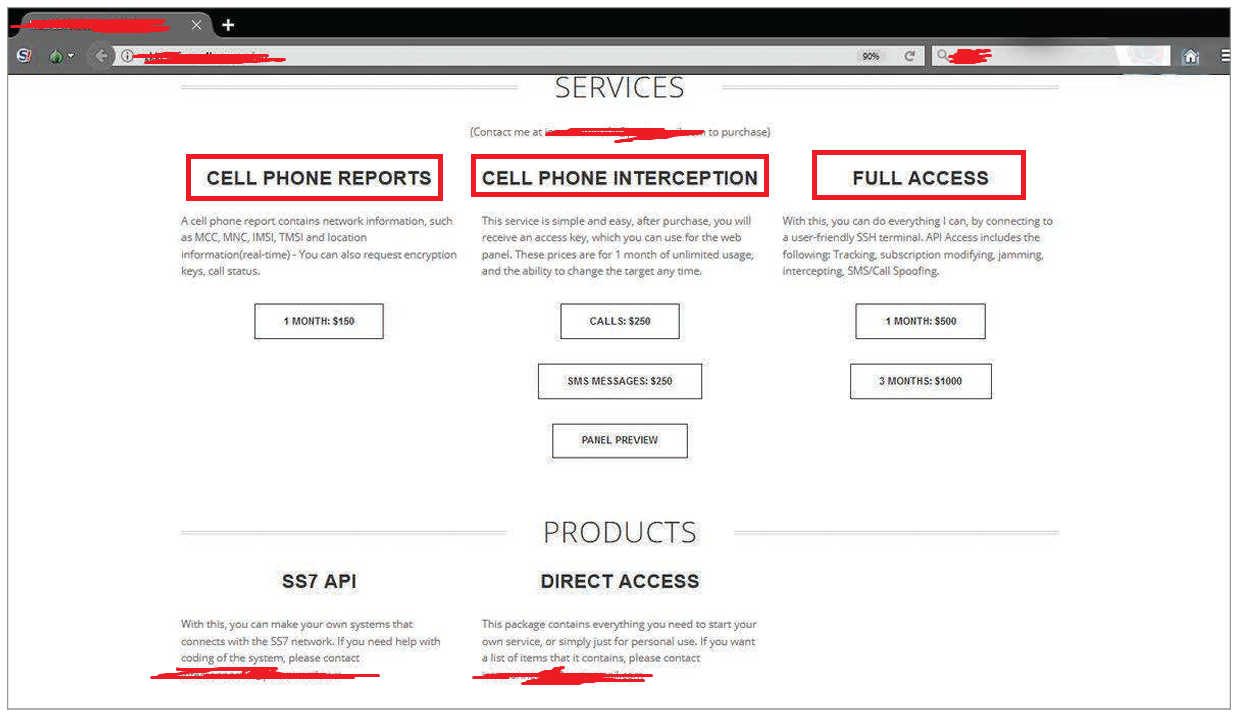
The SS7 network was once considered an environment that controls users’ access to network-based content and services, allowing licensed mobile operators to access customer data. However, many unlicensed entities currently […]

Many types of firewalls are often categorized by system protection, form factor, network placement, and data filtering method. Regarding 5G, Firewalls protect different network layers — especially in the Service-Based […]
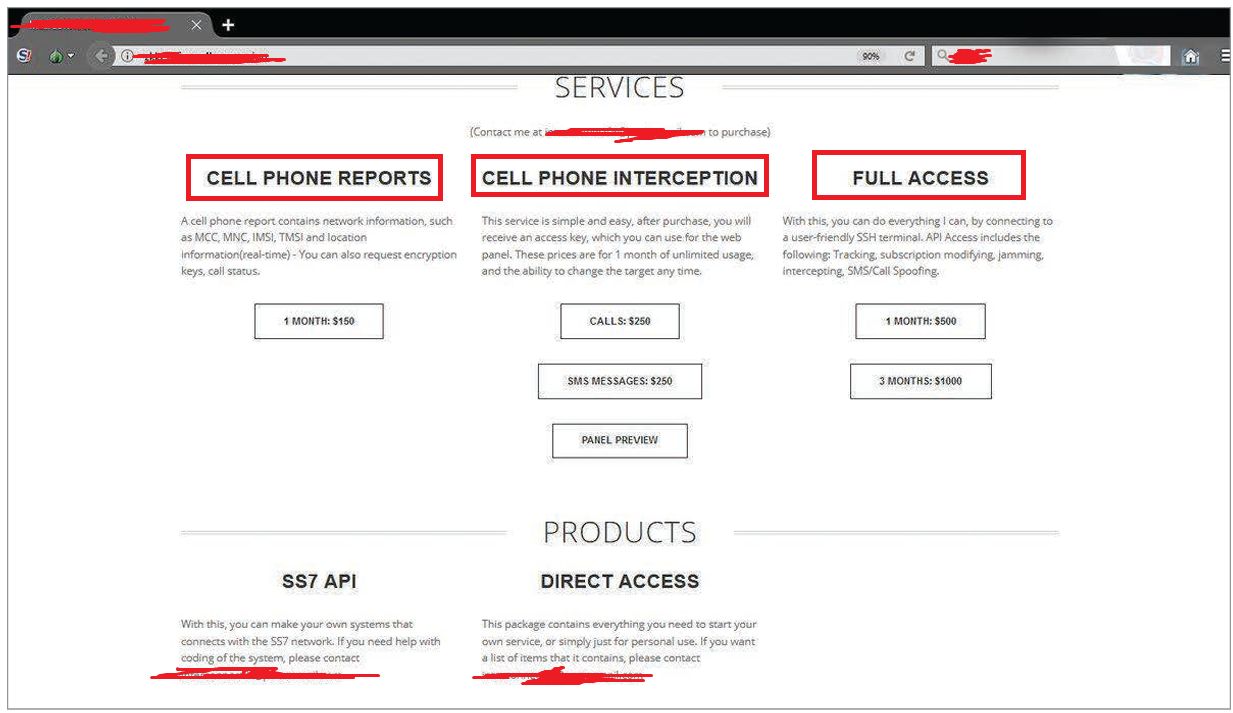
? The SS7 network was once considered an environment that controls users’ access to network-based content and services, allowing licensed mobile operators to access customer data. However, many unlicensed entities […]
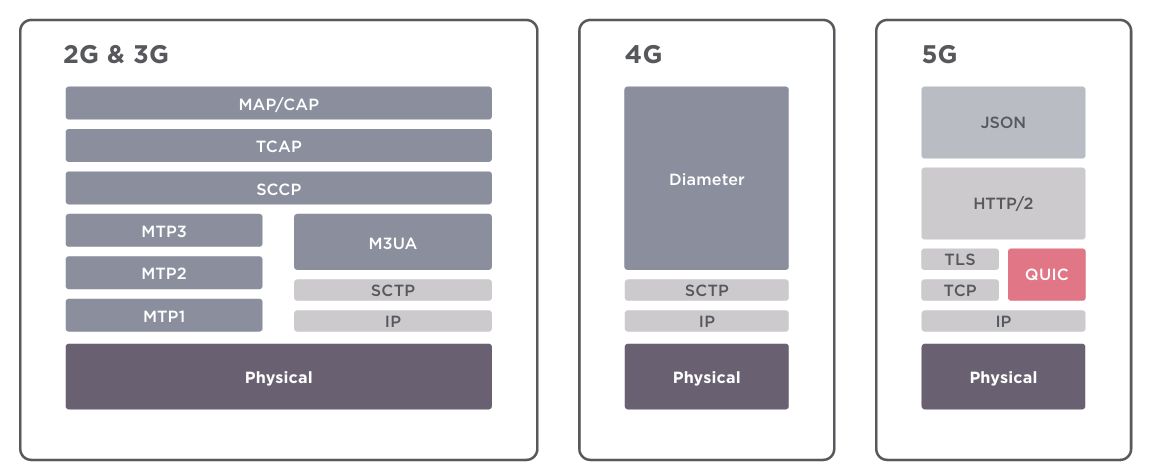
?Previous generations relied on the SS7 and Diameter protocols. The 5G network core is built on well-known Internet protocols such as HTTP and TLS. ? Security threats associated with 3G […]

?5Ghoul is the name given to a set of 14 newly discovered vulnerabilities in Qualcomm and MediaTek 5G modems, disclosed in December 2023 by researchers from the Singapore University of […]
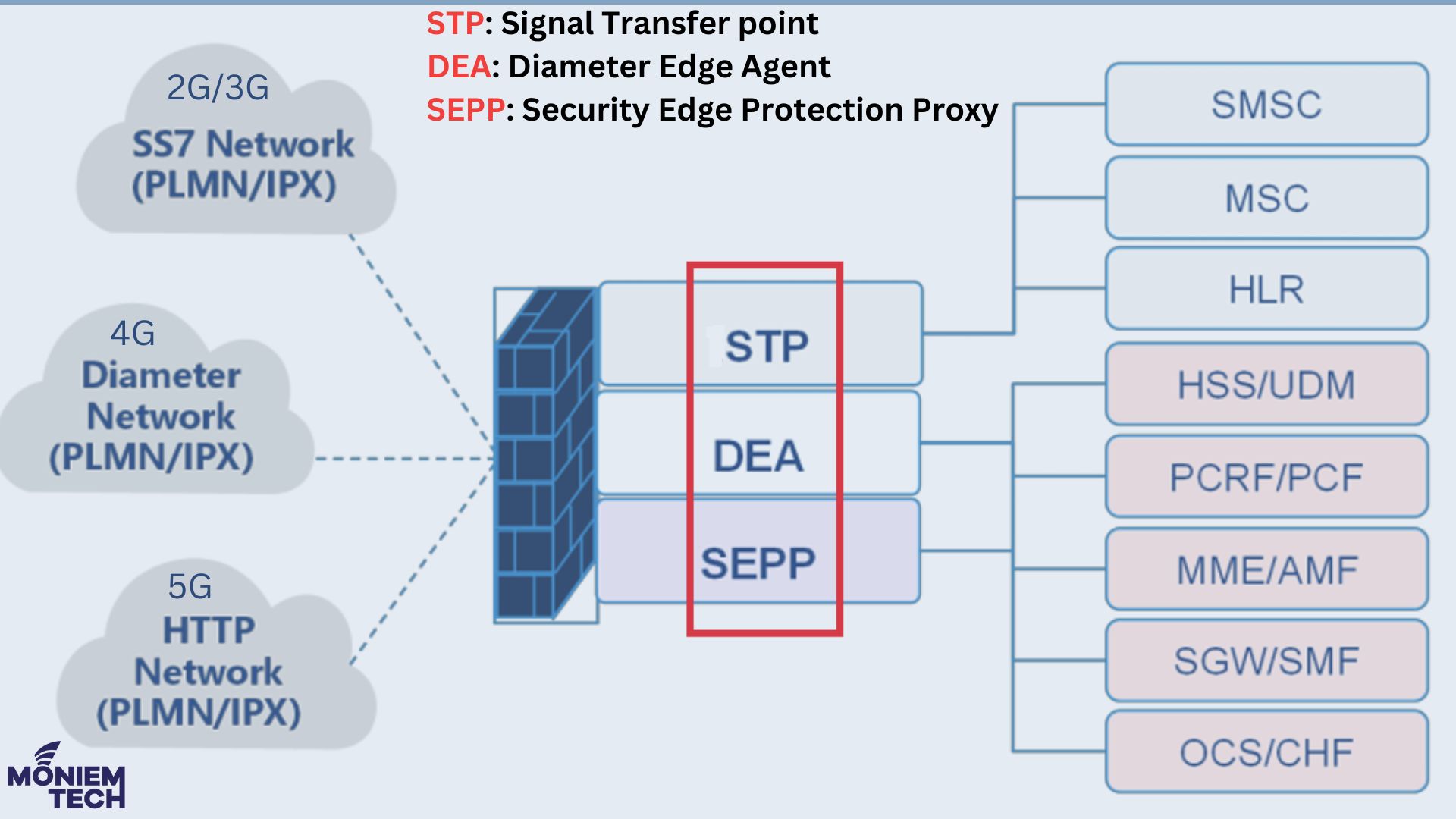
The journey started with 2G and 3G, where Voice was the leading service, and the main protocols were SS7 and SIGTRAN (Signaling Transport). At this time, the primary Firewalls are: […]

SS7 was never designed with security in mind, so it has always been open to internal and external threats. S7 Firewall is a smart, rules-based system that can monitor, create […]
